Hello, pals!
This is the story of Hannah, Hannah baker may Hannah also know about (.wav) file instead of using tapes…
Get to the point, it is a forensic write-up which starts from here:-}
I got this challenge from one of my college mates a week ago on WhatsApp group, listening through the audio file it’s a cool song with a knowledgeable rap about (.wav) extension. Let’s dive into it.
So it all starts with a huge audio file named MaroonDareFiveFSec.wav
Without any guess, I first put this file on the DeepSound app because of its extension(.wav). After extracting I got an MS Word file from this audio file named Hey.docx.
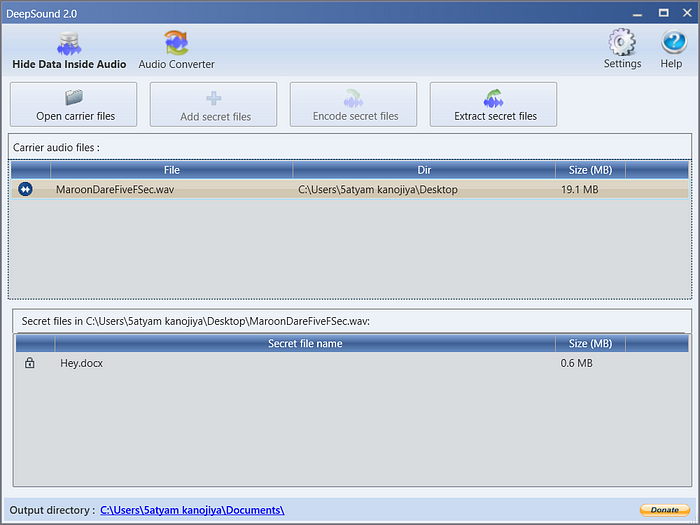
When opening Hey.docx it consists of 200 pages(approx.) full of encoding and the intro page looks like this:
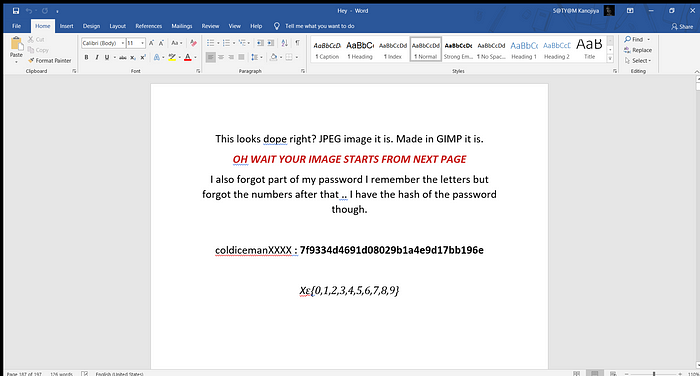
After reading this hint I can proceed further and from the next page, our image starts in the form of encoding. (I apologize for not providing the whole encoding due to its big size). But you can make a guess by viewing this:-
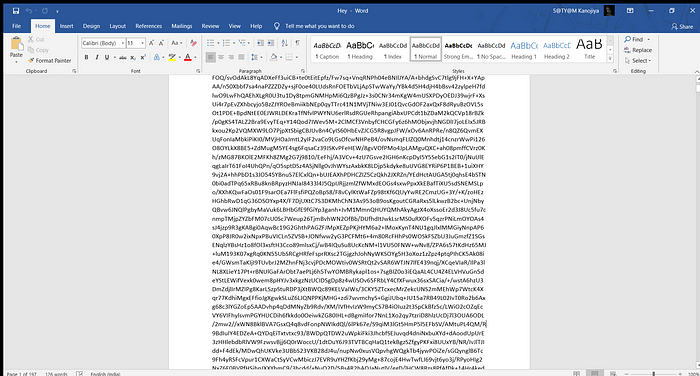
So, after reviewing it 2 or 3 times I decided to go with Base64 and head over to Base64Guru and got this…
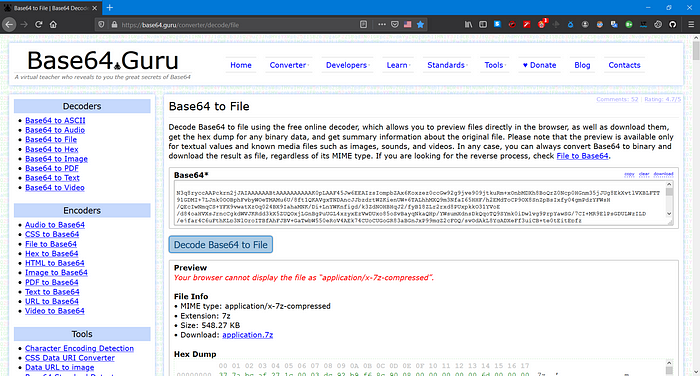
A zip file as shown in the above screenshot and by extracting got a text file.
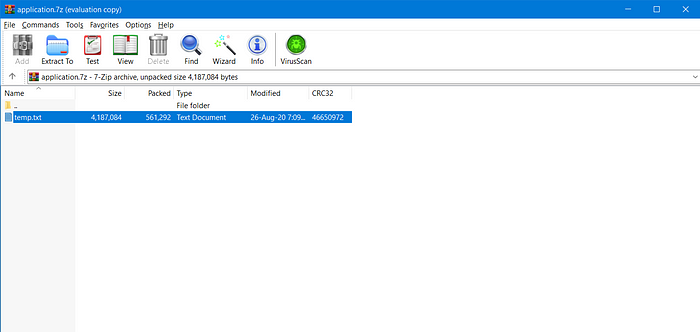
Opening this temp.txt file again a lot of encoding ><.
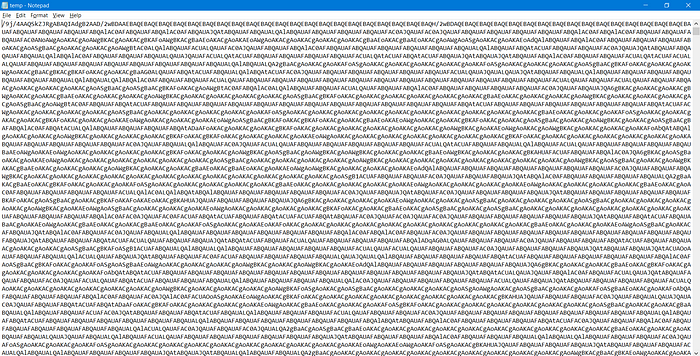
My brain is pinging me where is the image and again I took a shot with Base64Guru. Voilà!

But sadly this is not the end I forgot that it is not a flag then, I head over to image steg.
Note-There are many image stenography tools available on the internet but choose wisely for a particular approach/extension file.
Using steghide tool (Kali Linux) i got another JPG file named frigid.jpg but this time it is corrupted when looking through its magic bytes it didn’t match with JFIF/JPEG/JPG so by correcting it with help of hexedit, now frigid.jpg is viewable.
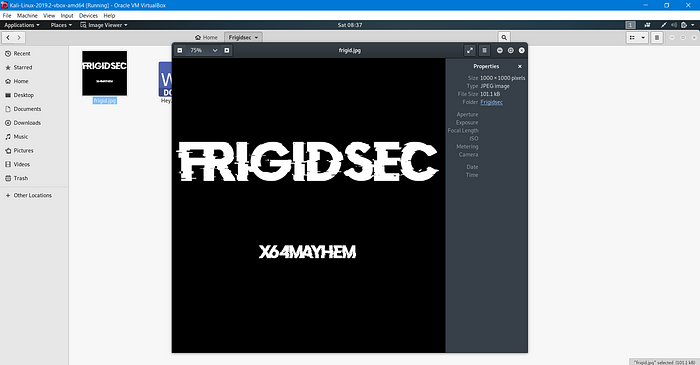
After spending 2–3 hrs on this image i didn’t get much info because I forgot to pay attention to the real character in the whole steg process. By doing steghide nothing came up.
So, remember our intro page ….???? Image for post

It said about password then my mind hit me with the idea of using stegcracker that is the one i didn’t try.
But it requires a word list to operate so head on to crunch tool because I had parameters to create wordlist as mentioned above in the screenshot. Every time brute-force is not the option. #Time_matters
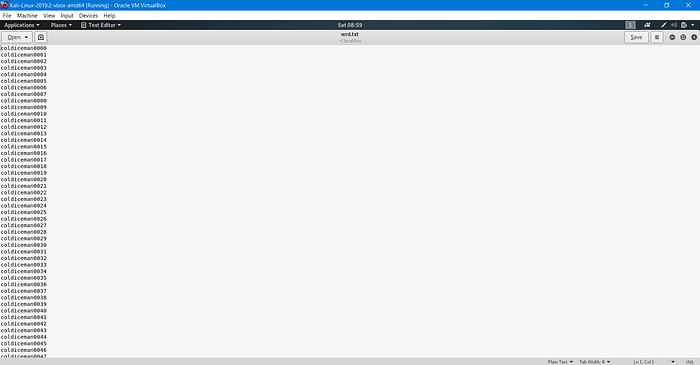
Using stegcracker with custom wordlist i finally got my flag in the form of frigid.jpg.out.
Hurrah!
Good job! So here is the flag…
F-Sec{1_g3t_h33b13_j33b1es_wh3n_d01ng_f0r3ns1cs_b77b7d86c10c}
It was a nice challenge and really enjoyed it!
Stay Hunting 💻
This article is written by Satyam Kanojiya and Taken from This Medium Post by the author hence do not come under Peer Review Policy. To check the profile of every writer of FrigidSec-Blog please visit HERE